 Overview:
Overview:
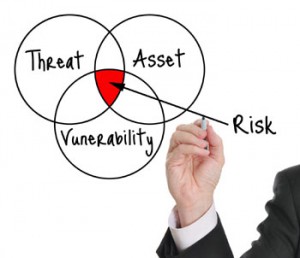
Vulnerability assessment is a process of identifying, quantifying and ranking the vulnerabilities in the system. Vulnerability assessment involves looking at the system elements and layout and their failure modes based on a given set of threats. Such assessments may be conducted on behalf of a range of different organizations, from small businesses up to large regional infrastructures. A systematic process, it analyses high-risk scenarios, characterizes the threat, and attempts to reduce the risk through the application of effective countermeasures.
Vulnerability Assessment will determine the highest vulnerabilities, how successfully an adversary could exploit these vulnerabilities, and the resulting damage due to an attack. The client can then utilize this to make a determination on how best to protect against these attacks given the risk/reward scenarios.
Assessments are typically performed according to the following steps:
• Assets and resources Categorization.
• Assigning quantifiable value and importance to those resources.
• Identifying the vulnerabilities or potential threats to each resource.
• Mitigating or eliminating the most serious vulnerabilities for the most valuable resources.
Vulnerability assessments should be performed against all information systems on a per-determined, regularly scheduled basis. While both security and vulnerability assessments may be performed by internal staff on an on-going basis, it is recommended that third parties should be retained periodically to ensure appropriate levels of coverage and oversight.